On July 29, 2025, Wiz Research revealed a major security flaw in Base44, the fast-growing vibe coding platform owned by Wix.
The vulnerability allowed attackers to bypass authentication and gain access to private apps and data, simply by using a public app_id. Wiz called it “remarkably simple to exploit.”
The issue was patched within 24 hours, with no evidence of real-world abuse.
What Wiz Is Saying
Wiz described the vulnerability in Base44 as critical, easy to exploit, and highly impactful. They emphasized that the flaw allowed unauthorized access to private apps using nothing more than a public identifier - no password, no secrets.
In their own words:
“This vulnerability we discovered was remarkably simple to exploit - it allowed anyone to register to an app with only a non-secret app_id. No password, secret, or any verification was required.”
“We reported the issue to Wix… and within 24 hours, a fix was deployed.”
Wiz credited Wix for their fast response and responsible handling of the disclosure.
What That Means (In Human Words)
Wiz researchers found a serious vulnerability in Base44 that let attackers reach into user apps easily-because the same unencrypted key was used by everyone. That key was exposed in the app URLs, making it possible for anyone to:
-
Use the key to register and verify an account
-
Create themselves as an admin on any user’s app
-
Bypass all password and SSO protections
No hacking. No passwords needed. One key unlocked thousands of apps.
Wiz called it an authentication bypass, and said the issue was “shockingly easy to exploit” across the entire platform. They alerted Base44 (which is owned by Wix), and the fix went live in less than 24 hours. Wiz also confirmed no customer harm was detected so fa
Bottom Line:
The issue was on Base44’s end - it was a platform-level security design flaw.
Base44 used the same static, unencrypted key for all customer apps built on the platform.
That key allowed admin-level access, and it wasn’t properly protected.
So no - individual users or developers who used Base44 did nothing wrong.
But because the key was shared across the whole platform, anyone who knew how to exploit it could gain admin control over any app built with Base44 - without needing to target a specific user or account.
This makes it a mass-level vulnerability, rooted in how the system was architected - not how it was used.
What You Need to Do to Stay Safe? Basically Nothing
As of July 2025, no action from Base44 users is required-they’ve fixed the issue platform‑wide.
That said, here’s what we recommend doing to be extra sure:
-
📝 Check your Base44 analytics dashboard-look for any unusual user visits or registrations to private apps that you built before July 9, 2025
-
🔍 Monitor access logs and patterns-for example, look for new admin accounts or registrations that didn’t go through your team.wiz.io
-
🚨 Enable platform monitoring or alerts-if you have Wiz or another cloud security tool, use it to spot unexpected Base44 app registrations or access.
✅ TL;DR
-
Fix status: Done. The patch was rolled out by Base44/Wix within 24 hours-no user action needed.
-
What else you can do: Review analytics and logs from before July 9 to spot odd activity.
-
Why it matters: Even if nothing happened, you should gauge exposure through audit logs and create better visibility next time.
Prompt It Up - keeping tabs
Worried your favorite tools might be exposed - and you won’t even know?
Here’s a prompt to help you scan the news like a pro:
“Show me the latest security vulnerabilities or breach reports related to [insert platform name here] from blogs, research firms, or security news in the last 30 days.”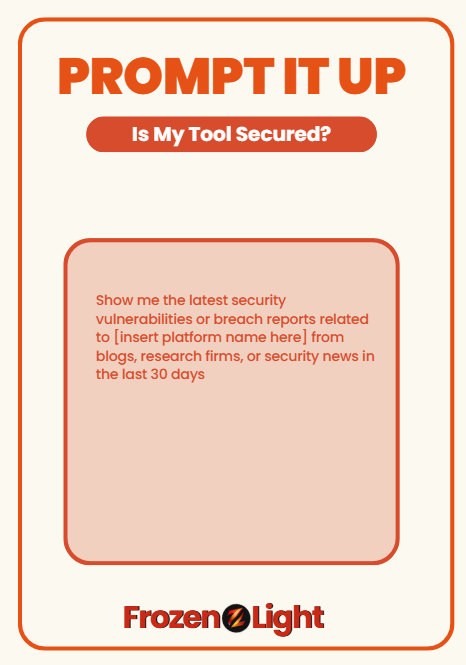
Use it in:
-
Gemini (best for live web + vendor blogs)
-
Perplexity (for fast security roundup)
-
ChatGPT (if browsing is enabled)
-
Or search manually on Wiz, BleepingComputer, and vendor blogs
📍Because when it comes to platform vulnerabilities, your dashboard won’t tell you.
But a blog post just might.
Frozen Light Team Perspective
This story isn’t about vibe coding gone wrong.
It’s about platform architecture - and the cost of moving fast without enough checks.
The Base44 vulnerability wasn’t caused by how users were building apps.
It wasn’t about prompts, blocks, or “vibes.”
It was about how the platform itself was built.
A hardcoded, shared, unencrypted admin key gave access to create superusers across every single app on the platform.
That’s not a feature misused - that’s infrastructure-level exposure.
This could’ve happened on any platform - low-code, full-code, vibe-based, or legacy - if the security wasn’t there from day one.
And that’s the deeper message here.
If anything, this story proves that growth speed can outpace security - especially when startups are racing into hot markets like solo app-building or AI-first creation tools.
The takeaway isn’t “don’t use vibe platforms.”
It’s know what’s under the hood before you build on it.
And if you’re scaling as a one-person business with AI and no-code platforms?
This is your reminder: trust is earned - not just hyped.